Pre-requisites
Terraform and AWS ECS
This document assumes you’re using Terraform to modify and deploy your AWS instructure. If you’re not using Terraform yet, you can set it up by reading this document. This document also assumes that you have already set up your ECS cluster, services, and tasks.- If you are not using ECS to run Mage, then this document will not apply for you. You can submit a feature request in our Slack channel if you want Mage to support deploying to your infrastructure through AWS CodePipeline.
- If you have not set up your ECS yet, you can check out this document to set it up with Terraform.
AWS CodeCommit
The pipeline that is created through the Terraform scripts has a AWS CodeCommit repo as a source. You will need to have a CodeCommit repo already set up that has your Mage repository code. Your CodeCommit repository should have a Dockerfile in the top level of your CodeCommit. Here is a reference Dockerfile that you can use for your own Dockerfile. You will also need to add abuildspec.yml file to your repository.
The buildspec.yml file can follow the following format:
AWS ECR
One pipeline created by the script will push a Docker build to AWS ECR, and the other pipeline will read from the same AWS ECR repo. Make sure you have already created your AWS ECR repository.Setting up AWS CodePipeline pipeline with Terraform
Use Terraform scripts in aws-code-pipeline folder to provision resources for AWS CodePipeline.Terraform plan
You can run the following command to see all the resources that will be created by Terraform:1. Environment variables
If you don’t have the AWS CLI installed, you’ll need to create this file:~/.aws/credentials.
In that file, add the following values:
2. Customize Terraform variables
In the file ./aws/variables.tf, you will need to update the default values for the following variables: AWS settings3. IAM Permissions
The IAM permissions are defined in theaws-code-pipeline/iam.tf file. Make adjustments to the
permissions as needed.
4. Apply Terraform
Using CLI- Change directory into scripts folder:
- Initialize Terraform:
- If you run into errors like the following:
then run the following commands to resolve this:
- If you run into errors like the following:
- Deploy:
Results
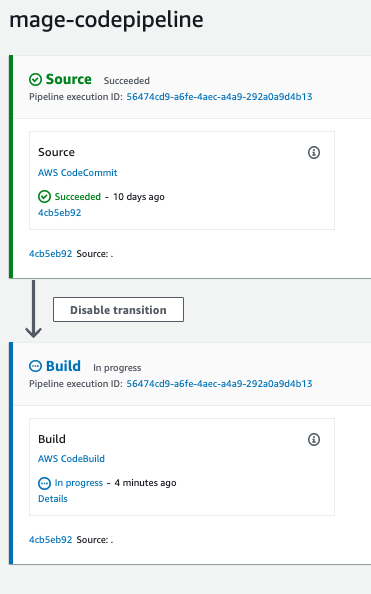
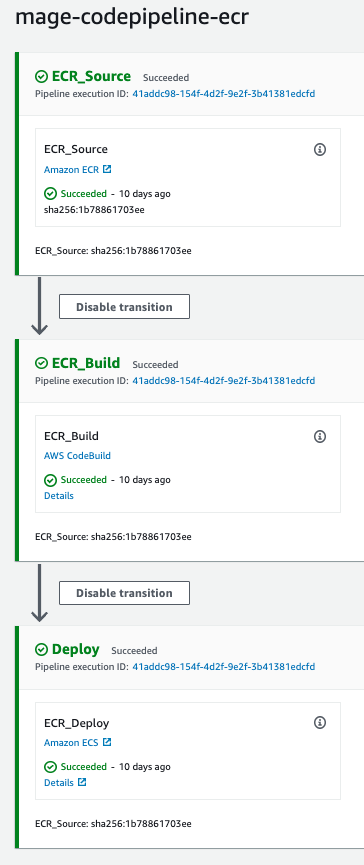
After running the Terraform script, you should see two AWS CodePipeline pipelines created,mage-codepipeline
and mage-codepipeline-ecr (unless you changed the code_pipeline_name variable). The mage-codepipeline pipeline
will be triggered every time a change is detected in the AWS CodeCommit repo. The mage-codepipeline-ecr pipeline
will be triggered every time a new image is pushed with into the AWS ECR repo.